There are reasons why USB or removable device usage typically banned in an organization. The common reason is for sanity, as we know that these devices can be the media of virus and malware to spread. There is also security reason, as sometimes people can put confidential data in these devices, which could easily be lost or stolen. Now if organizations wants to avoid such risks, IT administrator can always block USB or removable devices using Group Policy. This control can be the alternative to secure the network before implementing more complex security solutions like anti-virus or data loss prevention.
How to Block USB or Removable Devices using Group Policy
This scenario will demonstrate the way to completely block USB or removable devices in client PC. The client PC is running Windows 10 and joined to a domain named asaputra.com, where the Domain Controller is installed on Windows Server 2012 R2.
Using Group Policy Management Console in Domain Controller, the way to configure this Group Policy is pretty straightforward as the settings has been provided the settings under Computer Configuration > Policies > Administrative Template > System > Removable Storage Access.
As seen on the above screenshot, various settings for several device types has been preconfigured, such as removable disks (includes USB flash drive and external hard disk), WPD or Windows Portable Device (includes smartphone, music player, etc), CD and DVD, and even tape drives and floppy drives. Note that there are three types of deny action that we can choose:
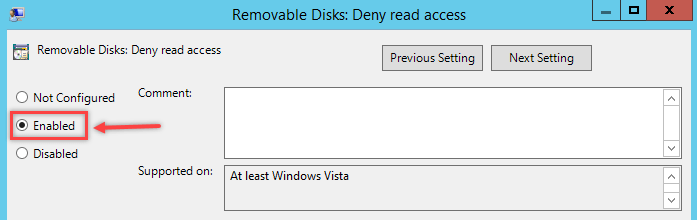
- Deny read access: Computer will totally block all users from reading contents in the removable storage. It also effectively prevents users from transferring anything from/to the removable storage. Administrator can use this if they want to completely restrict the usage of removable storage.
- Deny write access: Computer will prevent all users transferring anything to the removable storage, but not the other way around. Users will still be able to read contents in the removable storage. This action is suitable if the administrator only wants to protect confidential data in the computer from being copied out to a removable storage.
- Deny execute access: Computer will not prevent users from transferring anything from/to the removable storage, but it will block users from opening programs and files stored in the removable storage. This action is suitable if the administrator only wants to protect the computer from virus or malware that might be exist in the removable storage.
The right setting that match the scenario here is Removable Disks: Deny write Access. To enable it as shown below.
Policy must be applied at the computer level. When the policy has been applied, all logged in users will no longer have access to the USB flash drive or external hard disk attached on the computer. This message below will be shown in the client when they attempted to do so:
It is worth noting that administrator can also apply this policy at the user level, so each users may have different privilege on the computer. The settings can be found in User Configuration > Policies > Administrative Template > System > Removable Storage Access.
Notice that there are less available settings here compared to settings that can be applied at the computer level. At user level, we can only control read and write access, while at computer level we can also control execute access.
Troubleshooting
To force the policy update we can use command gpupdate /force in the command prompt as usual. In some case, the access rights may not be changed despite the policy has been applied. If this happens, then it may be required to also enable the setting to Set time (in seconds) to force reboot.
Computer will be forced to reboot after the defined time and the access rights will be changed afterwards. That’s pretty much all you need to know to block USB or removable devices using Group Policy.
You may also like -
Arranda Saputra
Latest posts by Arranda Saputra (see all)
- How to Move Documents Folder in Windows 10 - August 31, 2020
- How to Move Desktop Folder in Windows 10 - August 31, 2020
- Restore DHCP Server in Windows Server 2012 R2 - January 9, 2020