In a Microsoft Exchange Environment, AutoDiscover endpoint is the key for getting Outlook client work seamlessly with the Exchange Servers. These AutoDiscover endpoints are created in Active Directory for each server when you install CAS (Client Access Server) Role on them. Domain joined clients will use SCP entries in the Active Directory as a first thing and locate the AutoDiscover URL specific to the site scope. In some instances we may have to block clients form using SCP lookup to automatically configure Outlook. Once we block SCP lookup Outlook will determine the Service Binding Information or AutoDiscover URL using the SRV records in the DNS or deliberately trying the common autodiscover URLs. This article shows you how to disable Autodiscover SCP lookup using GPO.
Disable Autodiscover SCP Lookup using GPO
Group Policy is a hierarchical infrastructure that allows an Administrator having access to Microsoft Active Directory to implement specific configurations to the user and computers. It can also define user, security and networking policies at machine level. Group Policy Object is a collection of such settings that in effect on a Group of Users, OU or Computers. Controlling the SCP lookup behavior through GPO is not possible unless you import the specific group policy templates for each version of Outlook you are supposed to control. The AutoDiscover settings for Office 2013 and 2016 are built into the ADMX files for the entire Office package. Office 2007 and Office 2010 uses a special AutoDiscover ADM files. Below are the download location for the all the versions of Office since Office 2007.
Office 2007: https://download.microsoft.com/download/C/5/2/C5252326-202E-4674-A5A2-BC9F5C8F53BE/outlk12-autodiscover.adm
Office 2010: https://download.microsoft.com/download/C/5/2/C5252326-202E-4674-A5A2-BC9F5C8F53BE/outlk14-autodiscover.adm
Office 2013: https://www.microsoft.com/en-gb/download/details.aspx?id=35554
Office 2016: https://www.microsoft.com/en-in/download/details.aspx?id=49030
Importing ADM Template Files
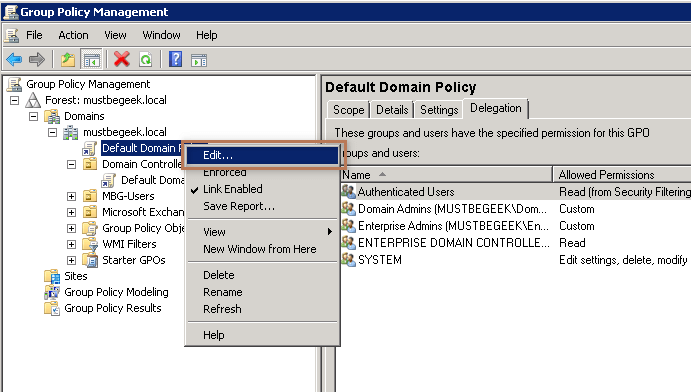
ADM Files are Stored in GPOs, you must load the. ADM files for each GPO for which you have to configure policy settings. To add the ADM template you must have necessary permission for the GPO Edit, Delete and Modify Settings. From the Group Policy. Management snap-in right click on the GPO for which you have to import the AutoDiscover ADM template and then click edit. In the Group Policy Object Editor → expand Computer Configuration → expand Policies → right click on Administrative Templates → Click Add/Remove Templates → Select the ADM file that you want to add, and then click Open as shown below. Repeat this step for each ADM files that you want to add and then click Close. You can then edit the added policy settings in the GPO. To learn how to install ADMX fiels, please see the TechNet article Loading the ADMX templates.
Exclude the SCP Object Lookup
Once the GPO templates are loaded, in the Group Policy Management. Editor navigate to User Configuration → Administrative Templates → Classic Administrative Templates →. Microsoft Outlook 2010 → Account Settings → Exchange → AutoDiscover → and then double click the AutoDiscover. Setting from the right panel. Now, enable the setting and then disable check box all other options except for “Exclude the. SCP Object Lookup” as shown below and then click OK
You can find the GPO settings under the Administrative Templates of User. Configuration similar to the above with some slight changes in the settings hierarchy. In this way you can disable Autodiscover SCP lookup using Windows GPO. Yo can also refer to the article Disable Autodiscover SCP Lookup using Windows Registry. This is suitable for disabling the. SCP lookup on a single machine rather than applying the settings to an entire organization.
Disable Autodiscover SCP Lookup using GPO (registry)
If you are hesitant to install the ADM or ADMX templates in your environment but still want to disable SCP lookup using GPO you do it by inserting a registry value. To do this, open the Group Policy Management as an Administrator. Find the GPO on which you have to implement the settings (in this article, I will be editing the Default Domain Policy) → right click on the Group Policy Object → click edit as shown below.
This will open the Group Policy Management Editor, expand User Configuration → expand Preferences → expand Windows Settings → right click on Registry → New → Click on Registry Item as shown below.
This will open the New Registry Properties, here in the Action select Create → in Hive Path Select HKEY_CURRENT_USER → in the Key Path, type Software\Microsoft\Office\X.0\outlook\Autodiscover → in the ValueName, type ExcludeScpLookup in the Value Type, select REG_DWORD and type 1 in Value Data fields as shown below.
You may note that in the Key path I have mentioned X.0 because the registry path varies based on the Microsoft Office version you are using. Replace the X.0 with corresponding to your version of Microsoft Office installation that you are targeting to block SCP lookup. You can get the version number for your office installation from the table below.
| Version Name | Version Number |
| Office 2007 | 12.0 |
| Office 2010 | 14.0 |
| Office 2013 | 15.0 |
| Office 2016 | 16.0 |
To verify this, logon as a user on which the policy is in effect and then type gpupdate /force in the command prompt.
Now, type “regedit” in Run (Win + R) and then press enter, browse to the path registry path HKEY_CURRENT_USER\Software\Microsoft\Office\X.0\outlook\Autodiscover (replace X.o with your version of Office). You will will see a DWORD “ExcludeScpLookup” added to the registry with Value 1 as shown below.
You can also enforce this registry update using the item level targeting as described in the article “Map Network Drive Using Item Level Targeting“. In this way you can disable AutoDiscover SCP Lookup using GPO.
You may also like -
Latest posts by Bipin (see all)
- Install Exchange 2019 in Windows Server 2019 - November 28, 2020
- Why Backup your Microsoft Office 365 - November 27, 2020
- What’s New in VMware vSphere 7 - September 18, 2020